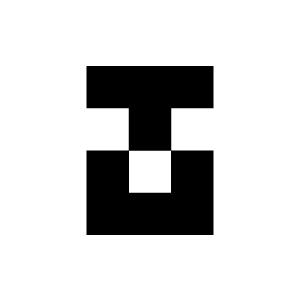
4.25
PII Tools Review
Considering PII Tools? Our review covers its security features, pricing, support, updates, and value for money. See if its automation suits your needs!

Comprehensive overview and target audience
PII Tools represent a critical category of software designed specifically to identify, manage, and protect Personally Identifiable Information within an organization’s data ecosystem. These tools scan diverse data sources, including databases, cloud storage, emails, and documents, to locate sensitive information like names, addresses, social security numbers, and credit card details. Understanding their function is essential before delving into specific solutions.
The primary target audience for PII Tools encompasses a wide range of roles and industries. Compliance officers in sectors like healthcare (HIPAA), finance (GDPR, CCPA), and retail rely heavily on these solutions to meet stringent regulatory requirements. IT security teams deploy them to minimize data breach risks and enforce data handling policies. Data governance professionals use them to map data flows and understand PII exposure. Essentially, any organization handling significant amounts of customer or employee data finds these tools invaluable for maintaining trust and avoiding penalties.
Central to their appeal are robust PII Tools security features. These often include advanced discovery algorithms using pattern matching, machine learning, and natural language processing to accurately detect PII, even in unstructured text. Many tools offer masking, redaction, or encryption capabilities directly within the platform, allowing organizations to secure sensitive data immediately upon discovery. Access controls and detailed audit logs are also standard, providing visibility into who accessed PII and when.
The landscape for these tools is dynamic, with vendors regularly rolling out PII Tools updates and new features. This continuous improvement cycle often brings enhanced detection accuracy for new data types, broader platform integrations (like SaaS applications or data lakes), and more sophisticated remediation workflows. Staying informed about these updates is key to maximizing the tool’s effectiveness over time.
Considering the complexity, comprehensive PII Tools support and training resources are crucial. Vendors typically offer documentation, knowledge bases, webinars, and dedicated support channels. Evaluating the quality and accessibility of these resources is important, especially for teams new to PII discovery and management concepts.
- Onboarding assistance
- Technical support responsiveness
- Availability of training materials
- Community forums
Finally, assessing PII Tools value for money requires looking beyond the initial cost. A thorough PII Tools pricing comparison should consider factors like the volume of data scanned, the number of users, the required features (discovery, remediation, reporting), and the deployment model (cloud vs on premise). While some solutions might seem expensive upfront, the potential cost of a data breach or non compliance fine often justifies the investment, making robust PII tools a financially sound decision for risk mitigation.
User experience and functional capabilities
Navigating PII Tools generally reveals a focus on simplifying complex data privacy tasks. While sophistication varies between vendors, many platforms strive for an intuitive interface, often featuring dashboards for a quick overview of PII risk posture and scan results. PII Tools user experience insights often highlight the importance of clear visualizations and straightforward workflow navigation. Getting accustomed to the specific terminology and configuration options might require an initial learning period, particularly for users new to data discovery concepts, but comprehensive documentation usually aids this process.
Understanding how to use PII Tools effectively starts with configuring scans. Users typically define the scope, specifying which data repositories like file shares, databases, or cloud buckets need examination. The tool then employs its detection engines, often combining pattern matching, keywords, and machine learning, to identify potential PII. Results are usually presented in detailed reports, pinpointing the location and type of sensitive data found. From there, administrators can initiate remediation actions such as masking, quarantining, or deleting the identified information directly through the tool’s interface, streamlining the response process.
Deployment follows a structured approach, often outlined in the PII Tools implementation guide provided by the vendor. Initial setup typically involves installing the software, either on premise or accessing a cloud instance, and then establishing secure connections to the target data sources. This requires appropriate credentials and network configurations. Configuring scan policies, detection rules, and user access permissions are critical next steps to tailor the tool to the organization’s specific compliance requirements and data landscape. Proper planning during implementation is key to a smooth rollout.
Despite their power, users might encounter common problems with PII Tools. Fine tuning detection rules to minimize false positives without increasing false negatives can be challenging and requires ongoing adjustment. Performance impact on scanned systems is another consideration, necessitating careful scheduling of scans. Integrating PII Tools with other tools within the security and data governance ecosystem significantly enhances their value. Connections to SIEM systems allow for centralized alerting, while integration with DLP solutions can enforce policies based on discovery findings. APIs often facilitate these connections, enabling a more unified data protection strategy.
Keeping abreast of PII Tools updates and new features is crucial for maintaining effectiveness. Vendors regularly enhance detection capabilities for emerging data types and regulations, improve performance, and add integrations. Adopting best practices for PII Tools usage maximizes their benefit. This includes:
- Regularly scheduled scans across all relevant data stores.
- Periodic review and updating of detection policies and rules.
- Implementing role based access control within the tool.
- Training relevant personnel on tool usage and PII handling procedures.
- Validating findings and remediation actions consistently.
Following these practices ensures the tool remains a vital component of the organization’s data privacy framework.
Who should be using PII Tools
Determining who benefits most from PII Tools requires looking at roles directly responsible for data protection and regulatory adherence. Primarily, compliance officers find these tools indispensable. They rely on PII Tools to automate the discovery and documentation needed to meet strict regulations like GDPR, CCPA, or HIPAA, simplifying audits and demonstrating due diligence.
IT security teams are also core users. Their focus is mitigating the risk of data breaches. PII Tools help them identify where sensitive data resides, often in unexpected locations, allowing them to apply appropriate security controls, access restrictions, and remediation actions like masking or deletion. Data governance professionals utilize the software to map data flows accurately, understand the organization’s PII footprint, and enforce data handling policies consistently across the enterprise.
Beyond these specific roles, any organization managing significant volumes of personal data should consider PII Tools. This includes sectors like healthcare handling patient records, financial services managing customer accounts, retail businesses processing transaction data, and even HR departments safeguarding employee information. A typical PII Tools use case scenario involves a company preparing for GDPR compliance: the tool scans all relevant repositories, identifies EU resident data, reports on its location and type, and facilitates necessary actions like obtaining consent or anonymizing data sets.
Effective implementation however depends not just on the tool but on the people using it. Personnel must be trained not only on the software’s features but also on the underlying principles of data privacy. Adhering to Best practices for PII Tools, such as regular scanning schedules, policy reviews, and validation of findings, is crucial. Therefore, users should include trained administrators capable of configuring the tool correctly and analysts who can interpret results and initiate appropriate responses, ensuring the technology truly supports the organization’s data protection goals.
Unique Features offered by PII Tools
Beyond core PII detection capabilities, the true power of PII Tools often lies in their adaptability and unique functionalities. Customization options allow organizations to tailor the software precisely to their specific data landscape, regulatory environment, and operational workflows. This typically includes defining custom data identifiers, creating nuanced detection rules to minimize false positives for industry specific terms, and configuring bespoke reporting templates that align with internal audit requirements or external compliance mandates. Fine tuning scan policies, setting risk thresholds, and managing user permissions are also common customization points, ensuring the tool operates efficiently and securely within the unique context of each business.
Unique features serve as key differentiators in the PII Tools market. Some vendors emphasize advanced machine learning algorithms for uncovering PII in unstructured data like images or audio files, while others might offer specialized remediation techniques such as irreversible data masking or secure data vaulting. Real time alerting, sophisticated risk scoring based on PII type and location, and integrated data subject access request DSAR workflows are other examples of features that can provide significant value. Evaluating these unique offerings is crucial when selecting a tool that best addresses an organization’s specific pain points and strategic data privacy goals. Effective Customizing PII Tools for business growth means leveraging these options to scale protection as data volumes and complexities increase, ensuring compliance keeps pace with expansion.
The ability for Integrating PII Tools with other tools is another critical feature area. Many solutions provide robust APIs or pre built connectors for seamless integration with existing security infrastructure, such as SIEM platforms, DLP solutions, ticketing systems, and data catalogues. This interconnectedness creates a more unified and responsive data protection ecosystem, enabling automated workflows and centralized visibility. While sophisticated features are common, there are also PII Tools for small businesses offering streamlined interfaces and essential functionalities, often with flexible deployment or pricing models suited to leaner operations. These versions still provide vital customization and integration points, making effective PII management accessible regardless of company size. Careful consideration of these customization options and unique integrations ensures the chosen tool delivers maximum impact.
Pain points that PII Tools will help you solve
Organizations today grapple with immense pressure to manage Personally Identifiable Information effectively. The sheer volume and distribution of data across fileshares, databases, cloud services, and communication platforms create significant challenges. Without automated assistance, identifying exactly where sensitive data like social security numbers, credit card details, or health records reside becomes a Herculean task, prone to human error and oversight. This lack of visibility is a primary pain point, leaving companies vulnerable and uncertain about their true risk exposure.
Navigating the complex web of data privacy regulations like GDPR, CCPA, and HIPAA presents another major hurdle. Demonstrating compliance requires meticulous discovery, accurate classification, and robust documentation, processes that are incredibly resource intensive when performed manually. Non compliance carries severe financial penalties and reputational damage. PII Tools directly address this pain by automating the discovery and reporting process, providing the evidence needed for audits and significantly reducing the compliance burden.
The constant threat of data breaches looms large. Sensitive data hidden in forgotten folders or unstructured text fields represents low hanging fruit for attackers. Manually securing every potential PII instance is impractical. PII Tools mitigate this risk by systematically scanning environments, pinpointing vulnerable data, and facilitating remediation actions like masking, encryption, or deletion. This proactive stance is crucial for preventing costly breaches. Furthermore, the challenge scales with company size; manual methods quickly become unsustainable. Thankfully, there are PII Tools for different businesses sizes, ensuring solutions can adapt. Effective Customizing PII Tools for business growth allows these solutions to evolve alongside increasing data complexity and changing regulatory landscapes.
Finally, inefficiency plagues manual PII management. Responding to data subject access requests or implementing data retention policies can consume excessive time and effort without the right tools. Security efforts can also become siloed. Integrating PII Tools with other tools like SIEM or DLP systems breaks down these barriers, creating a unified security posture where discovery directly informs threat detection and policy enforcement. By addressing these critical pain points, PII Tools empower organizations to protect sensitive data, ensure compliance, and operate more securely and efficiently.
Scalability for business growth
As organizations expand, their data footprint inevitably grows in both volume and complexity. PII Tools are designed with this expansion in mind, ensuring that data protection capabilities can keep pace with business ambitions. Scalability is not just about handling more data; it involves maintaining performance, accuracy, and compliance effectiveness across an evolving IT landscape. This includes scanning new data repositories, adapting to increased user loads, and managing a wider array of data types without degradation in service.
Modern PII Tools often employ architectures built for scale. This might involve distributed scanning agents that can be deployed across diverse environments, cloud native designs that leverage elastic resources, or efficient indexing techniques that minimize performance impact on source systems. This inherent flexibility allows businesses to confidently add new servers, cloud storage buckets, databases, or SaaS applications to their scan scopes, ensuring comprehensive PII visibility is maintained even during rapid growth phases. The ability to manage an increasing number of policies and remediation tasks centrally is also a key aspect of a scalable solution.
Furthermore, business growth frequently means entering new markets or handling different types of sensitive information, triggering new regulatory obligations. A scalable PII tool must adapt to these changing compliance requirements. Effective Customizing PII Tools for business growth enables organizations to define new detection rules, update policies, and generate specific reports needed for various jurisdictions or standards. This adaptability ensures continuous compliance. Thoughtful Customizing PII Tools for business scalability involves tailoring scan frequencies, detection sensitivity, and resource allocation to handle larger datasets efficiently, preventing bottlenecks and ensuring the tool remains a proactive asset rather than a reactive necessity. Investing in a solution that scales effectively is fundamental for sustainable growth, providing peace of mind that data protection will support, not hinder, future success.
Final Verdict about PII Tools
Navigating the modern digital landscape requires robust defenses for sensitive information. Organizations face escalating challenges from sprawling data volumes, complex regulatory demands like GDPR and CCPA, and the persistent threat of costly data breaches. Manually identifying and managing Personally Identifiable Information across countless files, databases, and cloud platforms is simply unsustainable and fraught with risk. PII Tools emerge not just as helpful utilities, but as fundamental components of a sound data governance and security strategy.
These solutions automate the critical tasks of PII discovery, assessment, and remediation. By leveraging sophisticated techniques including pattern matching and machine learning, they offer a level of accuracy and coverage unattainable through manual efforts. They provide essential visibility into where sensitive data resides, enabling organizations to effectively manage risk, streamline compliance reporting, and respond efficiently to data subject requests. While user experience can vary and may require initial acclimatization, the overarching aim is to simplify complexity, supported by vendor resources and training.
The true value extends further through customization and scalability. The ability to define specific detection rules, integrate with existing security ecosystems like SIEM or DLP platforms, and scale operations alongside business growth ensures that PII Tools remain effective long term investments. They address core pain points directly: reducing compliance burdens, minimizing breach potential, and improving operational efficiency in handling sensitive data. Choosing the right tool requires careful consideration of features, usability, support, and its capacity to adapt to evolving needs.
Our final verdict on PII Tools is clear: they are indispensable for any organization serious about protecting personal data and adhering to privacy regulations. The risks associated with inadequate PII management, including severe financial penalties and irreparable reputational damage, far outweigh the investment required. Implementing a capable PII tool provides the necessary automation, visibility, and control to navigate the complexities of data privacy effectively, making it a crucial element for modern business resilience and trustworthiness.
Advantage
Disadvantage
Find hidden PII across diverse data sources
Simplify compliance with GDPR, CCPA, and more
Significantly reduce data breach and privacy risks
Automate PII discovery, classification, and reporting tasks
Accurately identify sensitive data with high precision
Disadvantage
Potentially high cost for smaller organizations
Complex initial setup and configuration process
Risk of false positives requiring manual review
System performance may be impacted during scans
Integration with existing tech stack can be challenging
Rating
Free
$0 per Month Paid Monthly
- Up to 1000 files
- 1GB of files
- Manual data discovery
- No credit card required
Pro
$29 per Month Paid Monthly
- Up to 10K files
- Up to 10 GB
- Automated data discovery
- 7 day free trial
Business
$99 per Month Paid Monthly
- Up to 100K files
- Up to 100 GB
- Automated data discovery
- Integrate with other apps
- Share reports
Pro
$290 per Year Paid Yearly
- Up to 10K files
- Up to 10 GB
- Automated data discovery
- 7 day free trial
Business
$990 per Year Paid Yearly
- Up to 100K files
- Up to 100 GB
- Automated data discovery
- Integrate with other apps
- Share reports
Product Support
Web Based
Windows
Mac OS
Linux
Android
iOS
Phone Support
Email/Help Desk
AI Chat Bot
Live Support
24/7 Support
Forum & Community
Knowledge Base
Live Online
Documentation
Videos
In Person
Webinars
Implementation
Web Based
Windows
Mac OS
Linux
Android
iOS
Support
Phone Support
Email/Help Desk
AI Chat Bot
Live Support
24/7 Support
Forum & Community
Knowledge Base
Training
Live Online
Documentation
Videos
In Person
Webinars
Group text
Alternative Products
Frequently Asked Questions
What exactly is PII Tools?
PII Tools is a software solution designed to automatically scan various data sources (like files, databases, cloud storage) to detect and identify Personally Identifiable Information (PII) and other sensitive data types.
How can PII Tools help me?
It helps organizations achieve data privacy compliance (like GDPR, CCPA), reduce the risk of data breaches by locating exposed sensitive information, understand where their sensitive data resides, and implement data minimization policies.
Who is PII Tools best suited for?
It’s ideal for businesses and organizations handling sensitive customer or employee data, particularly those needing to comply with data privacy regulations, including compliance officers, IT security teams, and data privacy professionals.
What are the main features highlighted in the review?
The review highlights its comprehensive scanning across diverse data sources/file types, customizable detection rules, detailed reporting dashboards, and high accuracy in identifying various PII types.
How accurate is PII Tools at finding sensitive data?
The review suggests it offers high accuracy using advanced algorithms and patterns, though acknowledges the possibility of occasional false positives/negatives, often with adjustable sensitivity.
Is PII Tools easy to set up and use?
The review generally portrays it as relatively user-friendly with a straightforward setup and intuitive interface for core tasks, although advanced configuration might be more complex.
What are the pros and cons mentioned in the review?
Pros: Comprehensive data discovery, strong accuracy, aids compliance, user-friendly interface for core tasks, good reporting. Cons: Potential cost, possibility of false positives/negatives requiring manual review, complex advanced configuration, potential integration limitations.
Based on the review, is PII Tools worth it?
Yes, the review concludes that for organizations serious about data privacy, security, and compliance, the investment is often justified as a crucial safeguard against breaches and fines, making it a worthwhile solution for its target audience.